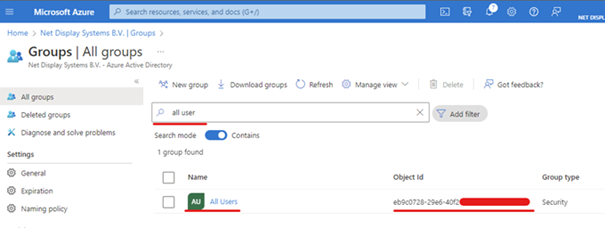
Azure settings
It is necessary to configure the Azure instance to allow users within yourorganization to access the PADS4 (Legacy) CMS application. To enable this, please follow the steps in this document :Step 1 : Navigate and login to your “Azure portal” page as an admin
https://portal.azure.com/Step 2 : Select the “Microsoft Entra ID” option

Step 3 : On the left hand side panel, select “Enterprise Applications”
Important
Step 4 : Select the ”+ New application” option at the top of the screen

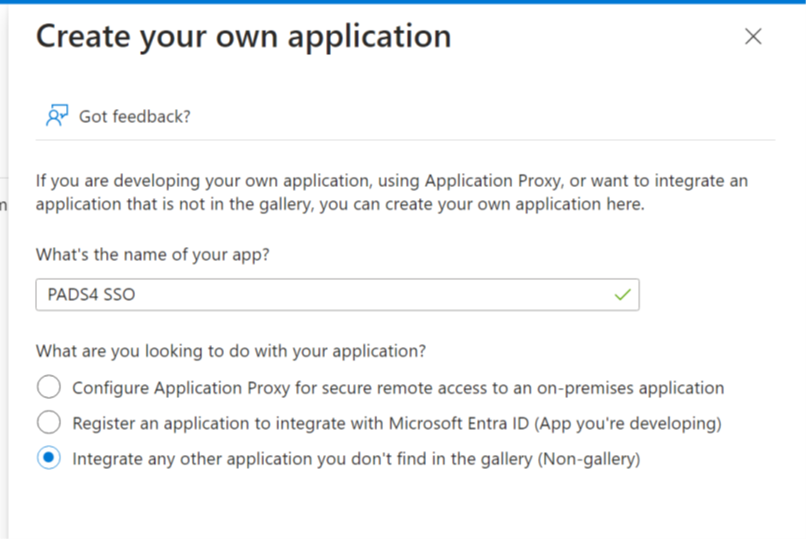
Step 5 : Click on “Create you own application”

Step 6 : Fill in the information requested in the form and click create
Step 7 : Creating a connector group / application proxy connector:
Select the Manage Application Proxy Connectors section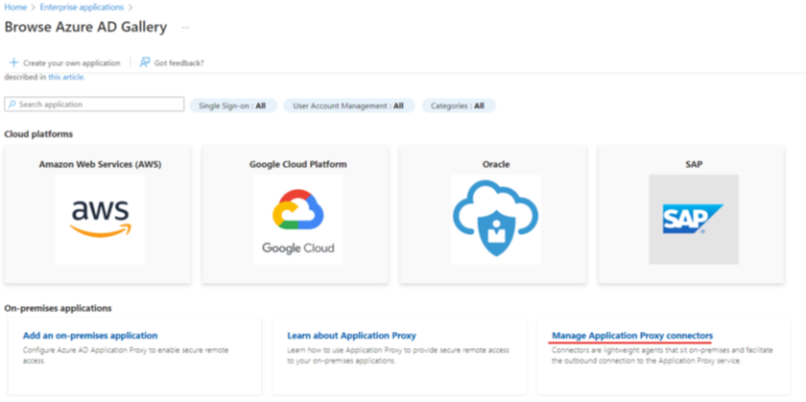
- In the Application Proxy menu, Select the + Download ConnectorService
- Agree to the terms and download the AADApplicationProxyConnectorInstaller.exe file to the server PC.
-
Run the installer and make sure to validate your Azure Administratorcredentials during the setup.
- After the installation is complete, select the +New Connector Groupsection
- Create a default name for your connection. For example : SSO Connector
- Select your server machine from the Connector list
-
Select the region where your machine resides.
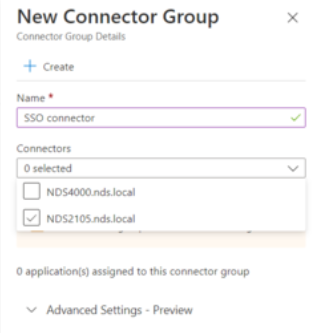
- Save your new connection here.
- Head back to the Enterprise Applications section, and select the “Add your own on-premises application”
Creating an on-premises application within Azure
-
Select Add an on-premises application
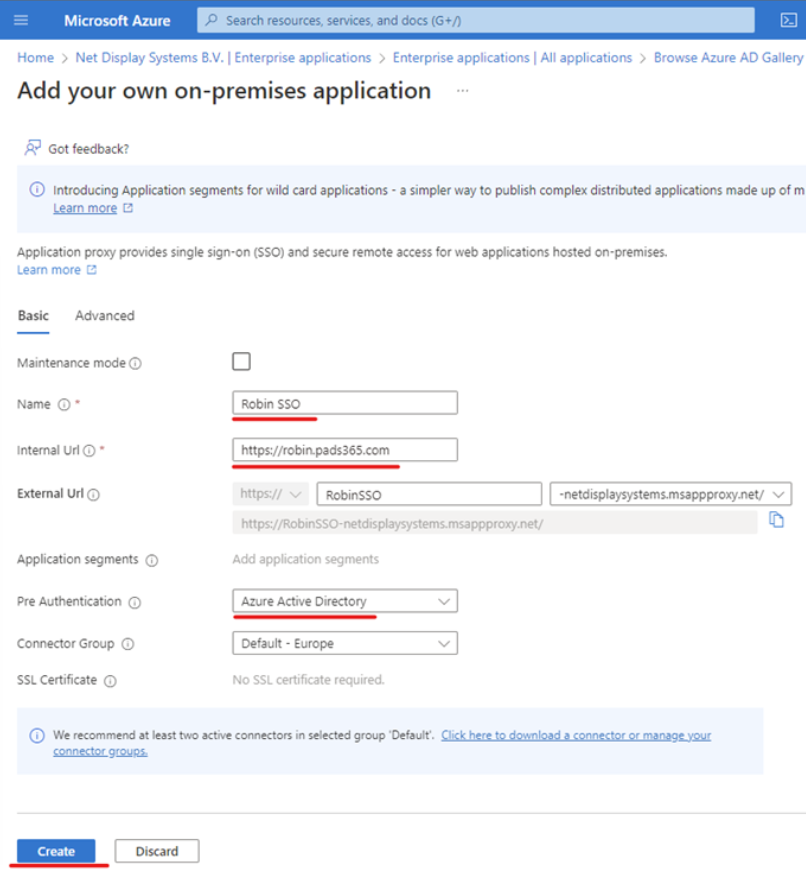
Step 8 : Fill in the information requested in the formand click create.
Example :
Name : PADS4 CMS Internal URL : URL of the PADS4 CMS installation (https://servername) Pre-authentication : Azure Active Directory Connector Group : SSO Connector (default). This is the connector group you have just set up Then Click on the add buttonStep 9 : Navigate to the newly created application
- Navigate to the newly created application by selecting “ Enterprise Applications” and use the search bar to find your application. Select it and then navigate to “Users and Groups” :
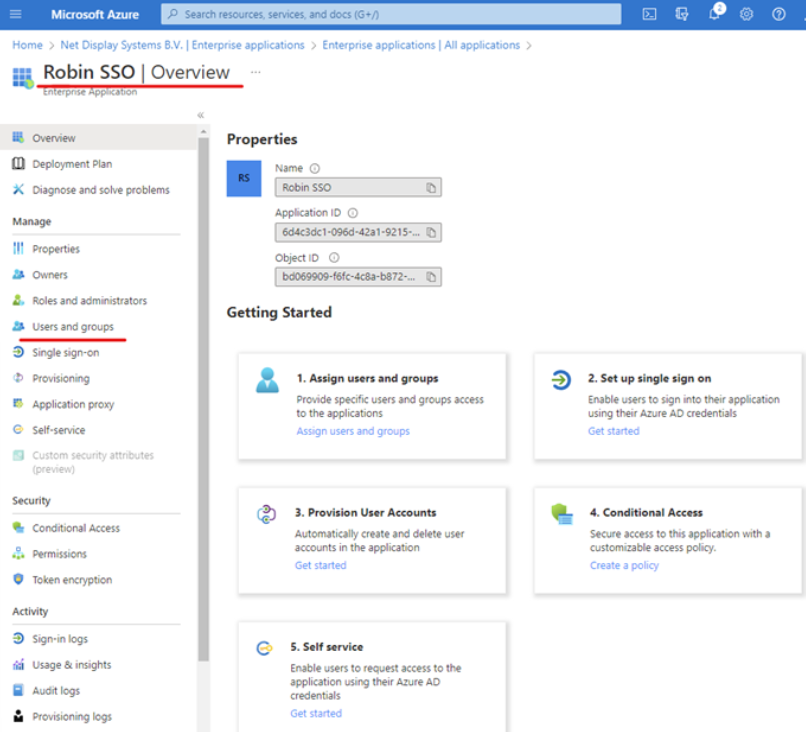
- Add the users and groups that will have access to the application byselecting the “ Add user/group ” option
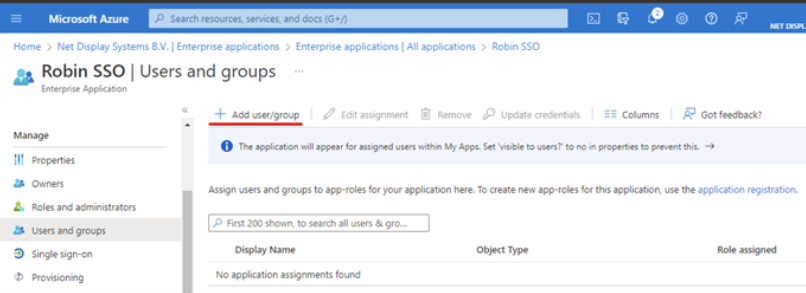
- Select “None Selected” option to gain access to the groups and users :
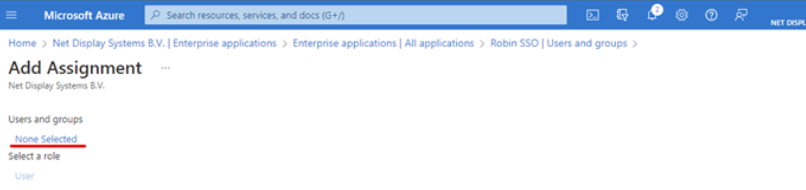
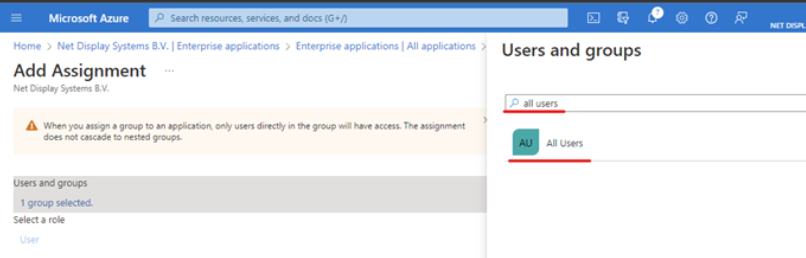
- Use the search bar to search for a user or group. Click “select” and “assign” upon completion
Step 10 : To configure Single Sign On (SSO)
Select “Single sign-on option” in the left pane and then “SAML”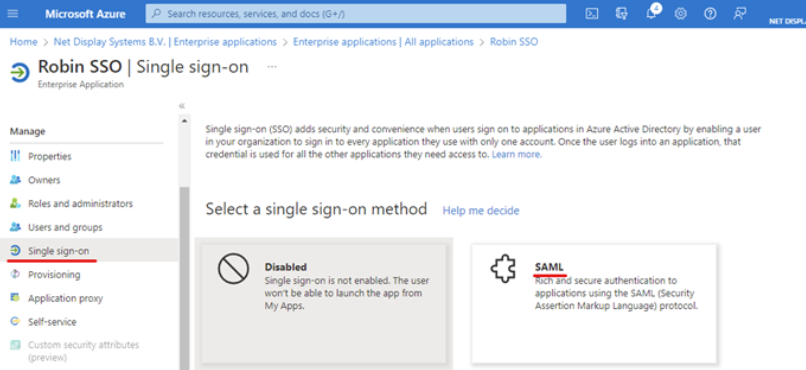
Step 11 : Select “Edit” on the “Basic SAMLConfiguration”
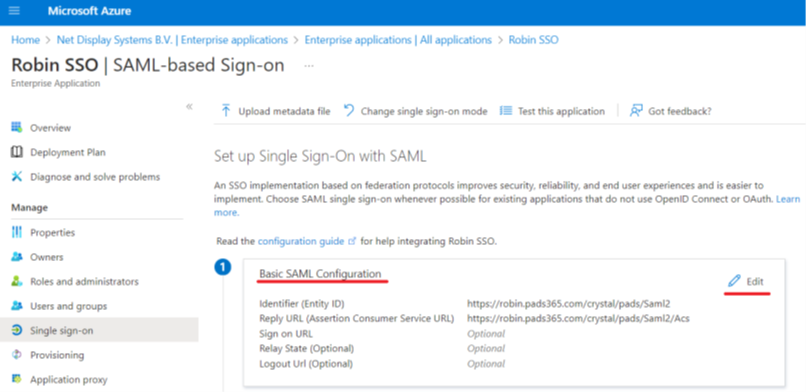
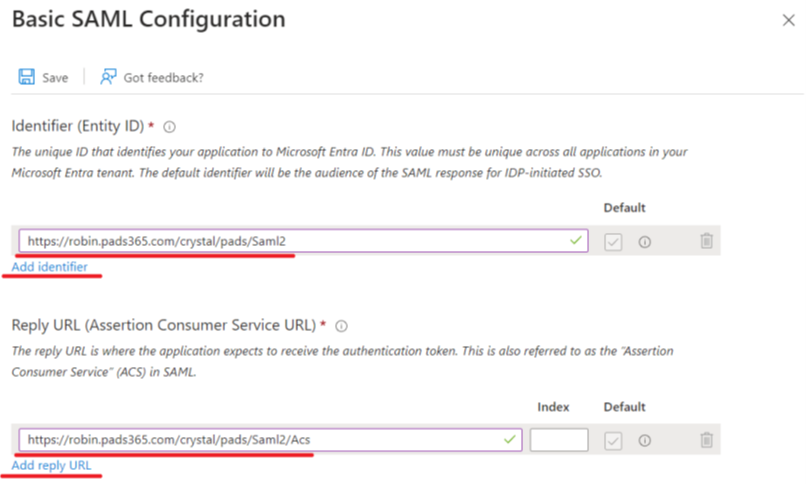
Example :
Identifier: Local PADS4 CMS URL with /Saml2 (e.g: https://robin.pads365.com/crystal/domain/Saml2) If a unique network port is being utilized, be sure to include this in above string. E.g : https://robin.pads365.com:444/crystal/domain/Saml2 Make sure you specify your PADS4 domain at “domain” in theURL
Remark : If you have configured SSO on a version before 2023.1, the domain name wasn’t required in the URL when using only one domain. From version 2023.1 onwards, the domain name is required in the URL both for one and multi-domain setups.Therefore, when updating from a version before 2023.1 with SSO configured, to the latest release, make sure to add the domain to both the Identifier and Reply URL.Be sure to “Save” these configurations.
Step 12 : Whilst in the “ Single sign-on ” menu, select “Edit ” on the “ Attributes & Claims ” section.
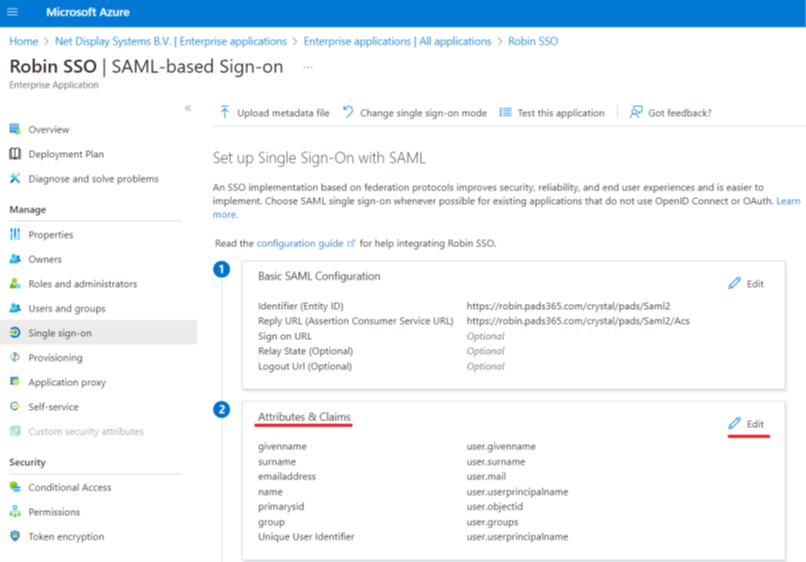
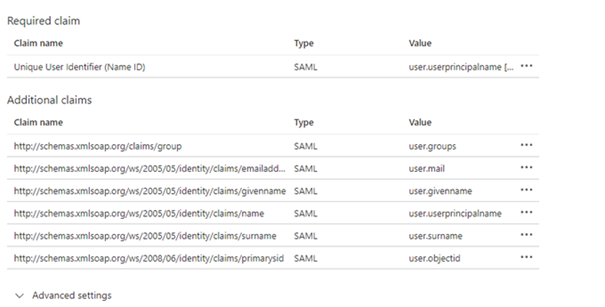
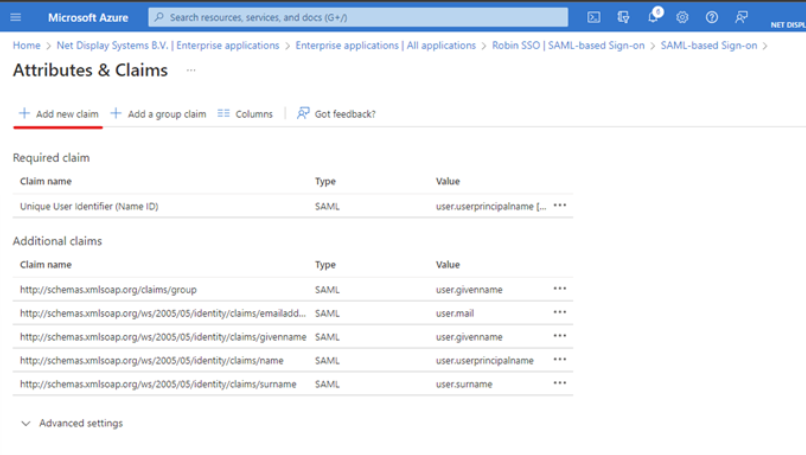

Add / Edit the “group” claim detail as per below example and save
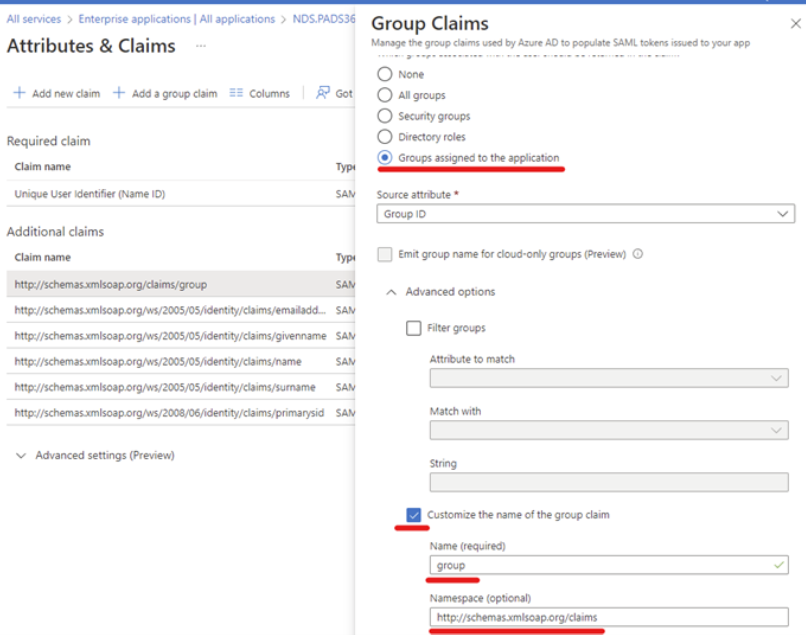
Remark : If you now experience the following behavior, the SSObutton on the login page works and you are able to input yourcredentials but it will get redirected to the PADS4 Login portal with “Noaccount is defined for your authentication request” in the URL.There can be 2 causesthe group claim is incorrectly configuredThe user you are trying to log in with has the same email addressalready configured to a CMS / Workspace user.
You have now prepared SSO within Azure for your PADS4Application.
Information Required for SSOConfiguration in PADS4 CMS
In order to configure SSO within PADS4 CMS,you will require the following :
Certificate of the federation server Federation Service Identifier SAML SSO URL Metadata URL URL of the Relying party and; Group ID of the User Group you have assigned to the application.1. Obtaining the “Certificate of the federationserver”
Within your application, select “ Single sign-on ” in the left pane Scroll down to the “ SAML Certificates ” heading Select the “ Download ” option next to the “ Certificate (Raw) ” option.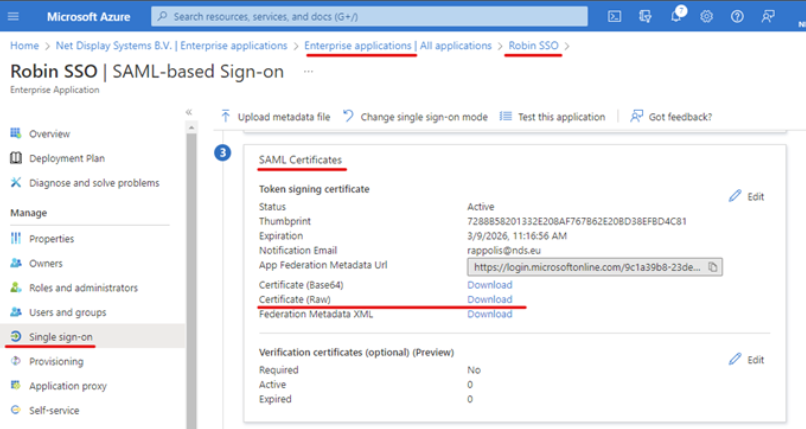
2. Obtaining the “ Federation Service Identifier ”
Within your application, select “ Single sign-on ” in the left pane Scroll down to the “Set up“ your_application_name ” heading Select the “ Copy ” option next to the “ Azure AD Identifier ” option.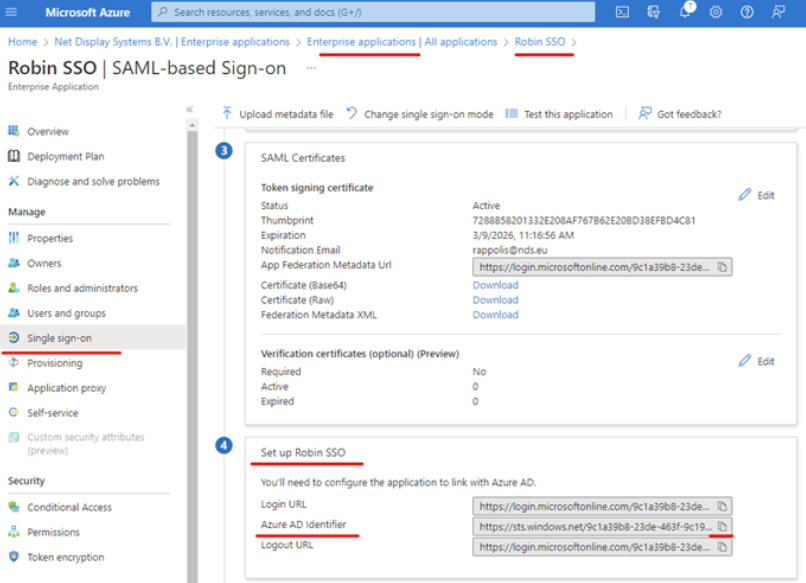
3. Obtaining the “SAML SSO URL”
Within your application, select “ Single sign-on ” in the left pane Scroll down to the “ Set up “your_application_name ” heading Select the**“ Copy ”** option next to the “ Login URL ” option.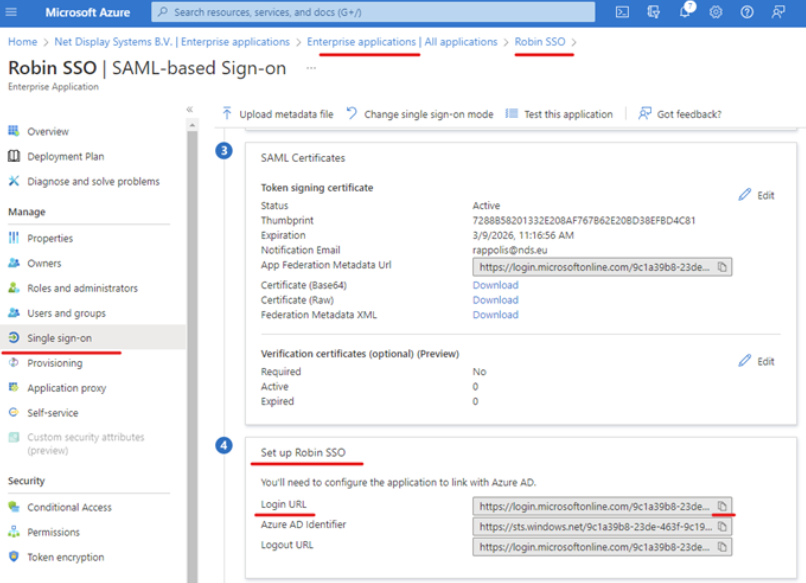
4. Obtaining the “Metadata URL”
Within your application, select “Single sign-on ” in the left pane Scroll down to the **“ SAML Certificates ” **heading Select the “ Copy ” option next to the “ App FederationMetadata URL ” option.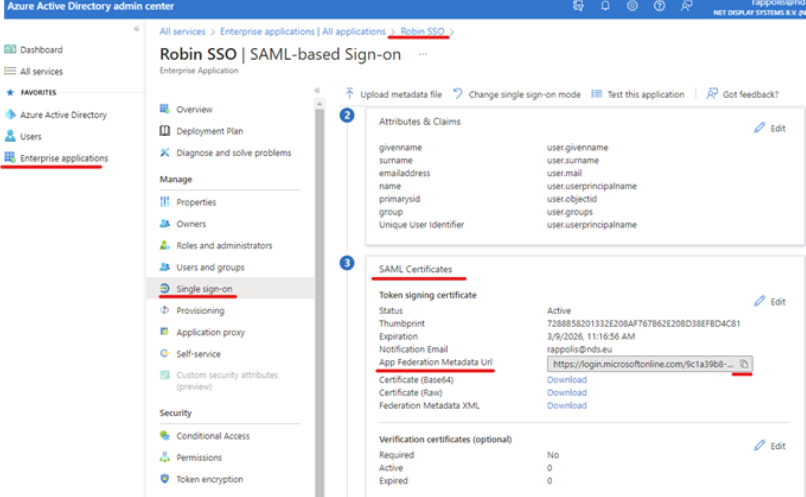
5. Obtaining the “URL of the Relying party”
Within your application, select “ Single sign-on ” in the left pane Scroll to the “ Basic SAML Configuration ” heading Copy the string next to the **“ Identifier (Entity ID) ” **option.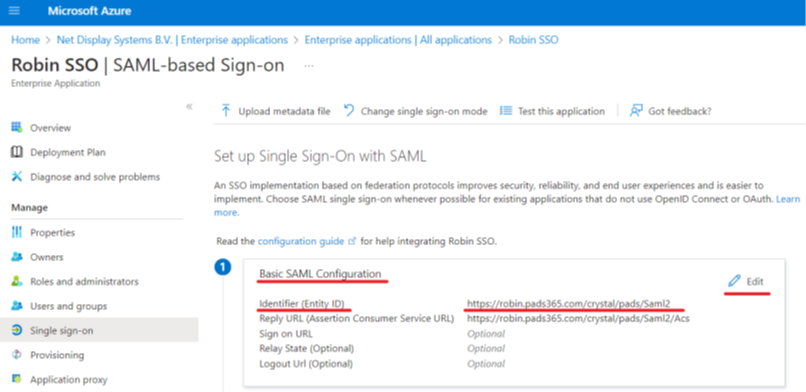
6. Obtaining the “Group ID” of the group you assigned to your application:
For every user group added to utilize the PADS4 CMS application, a mapping table will be required to add the groups to the interface. Please provide the installers the Group ID’s and names of the Groups from Azure to ensure users will be able to login.