Skip to main contentThis manual provides step-by-step instructions to configure Single Sign-On (SSO) for PADS4 using Microsoft Entra ID (formerly Azure Active Directory).
1. Azure Configuration (Microsoft Entra ID)
To enable access to PADS4 through Microsoft Entra:
Step-by-step
- Go to https://portal.azure.com and sign in as an administrator.
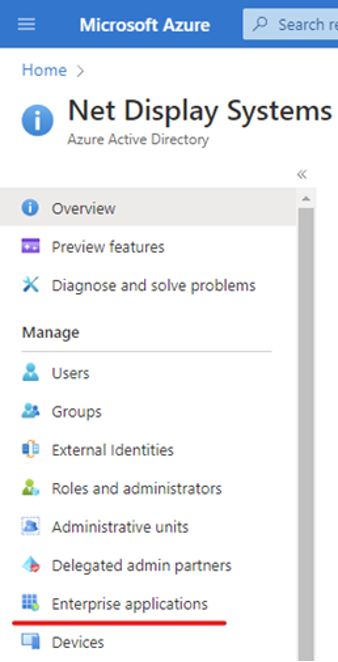
- In the left menu, select Microsoft Entra ID.

- Select Enterprise Applications.
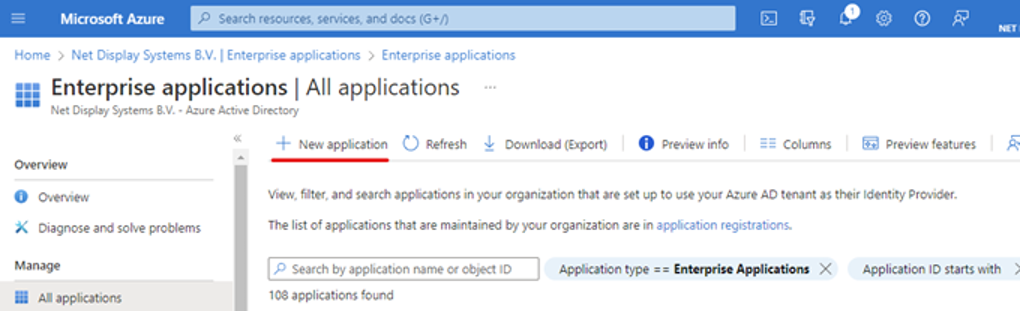
- Click + New Application.
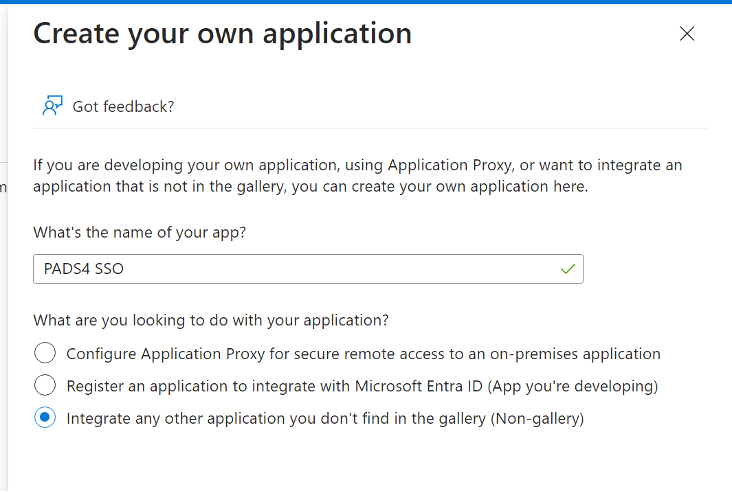
- Choose “Create your own application”.

- Fill in the information for the form
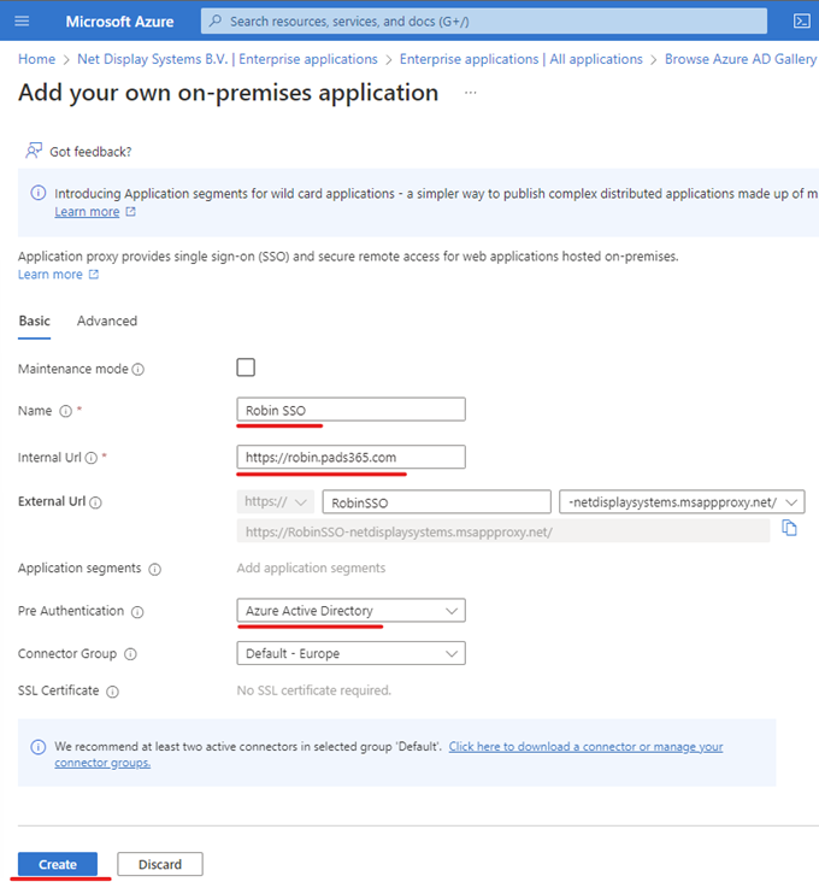
- Click Create
Assign Users & Groups
- Open your newly created application by going back to Enterprise Applications and searching for it.
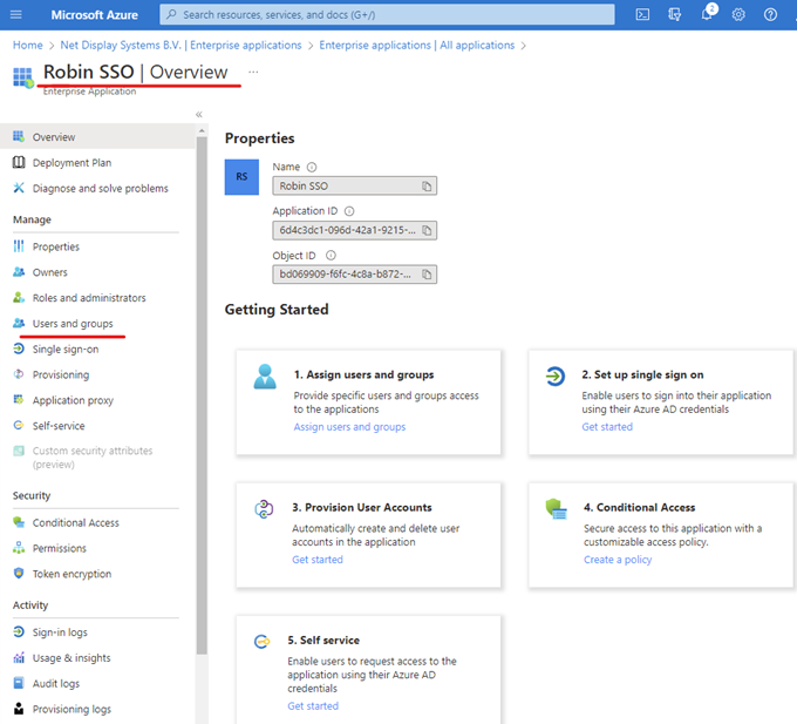
- Select Users and Groups.
a. Click Add user/group.
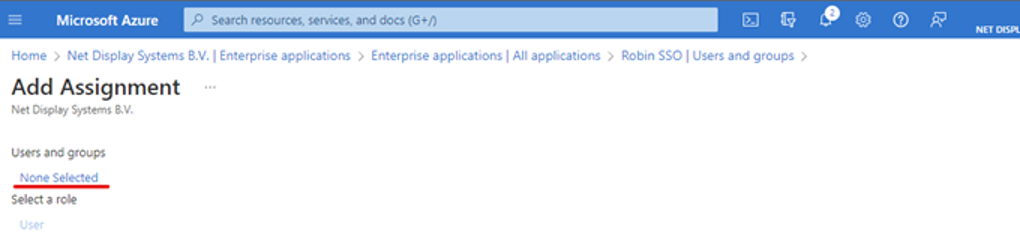
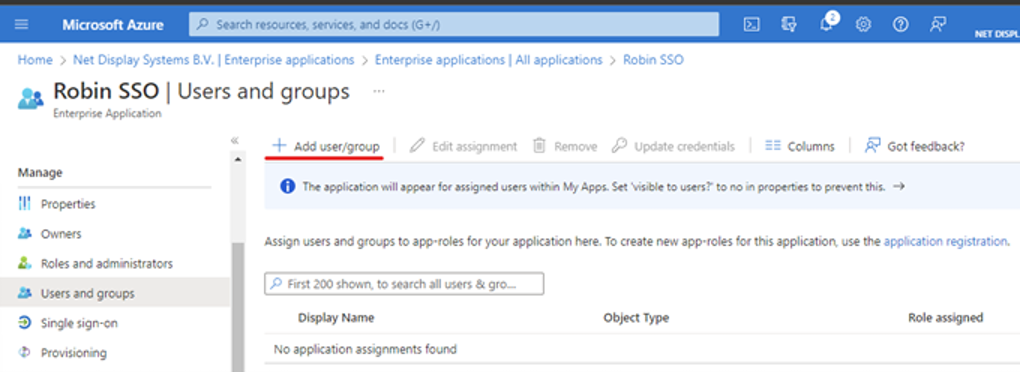 b. Select None Selected, then search and select users or groups.
b. Select None Selected, then search and select users or groups.
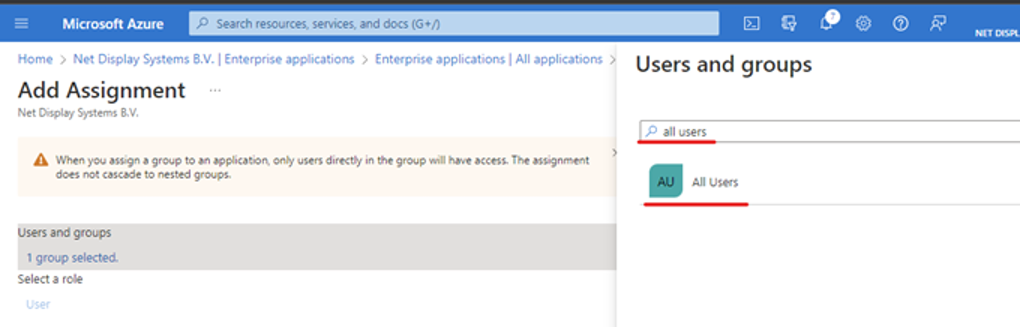
 c. Click Select, then Assign.
c. Click Select, then Assign.
💡 Tip: Create a dedicated PADS4 CMS group in Windows Server AD and assign it here.
- Go to Single sign-on in the left pane.
- Choose SAML.
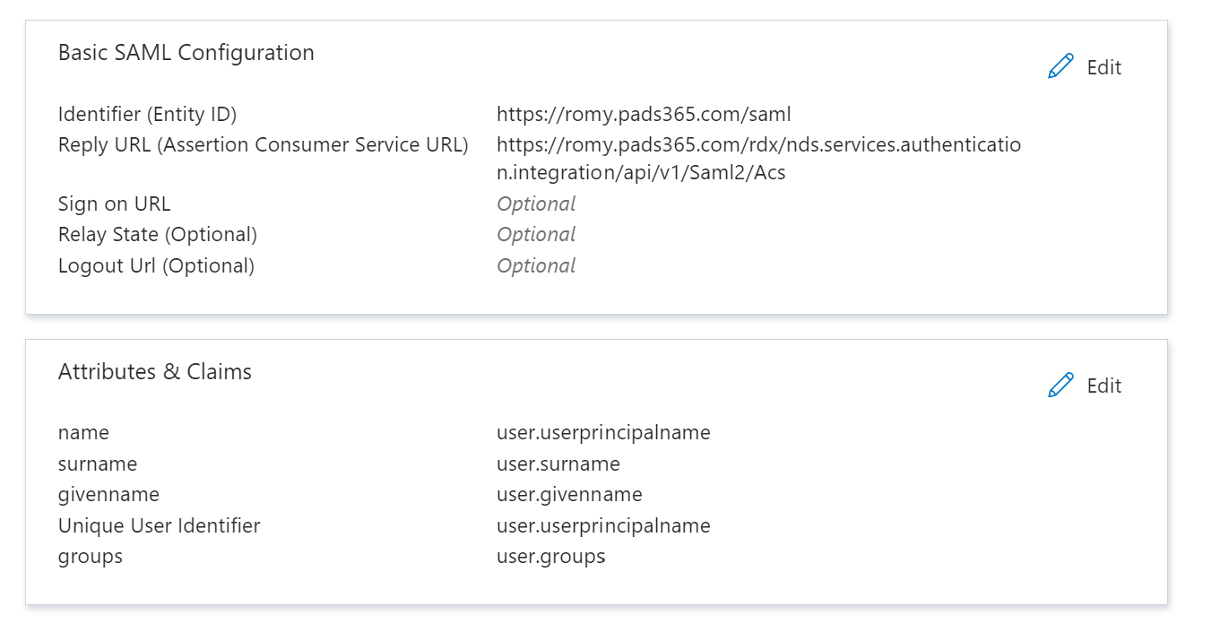
- Under Basic SAML Configuration, click Edit and add:
- Identifier (Entity ID):
https://romy.pads365.com/saml
- Reply URL:
https://romy.pads365.com/rdx/nds.services.authentication.integration/api/v1/Saml2/Acs
Click Save.
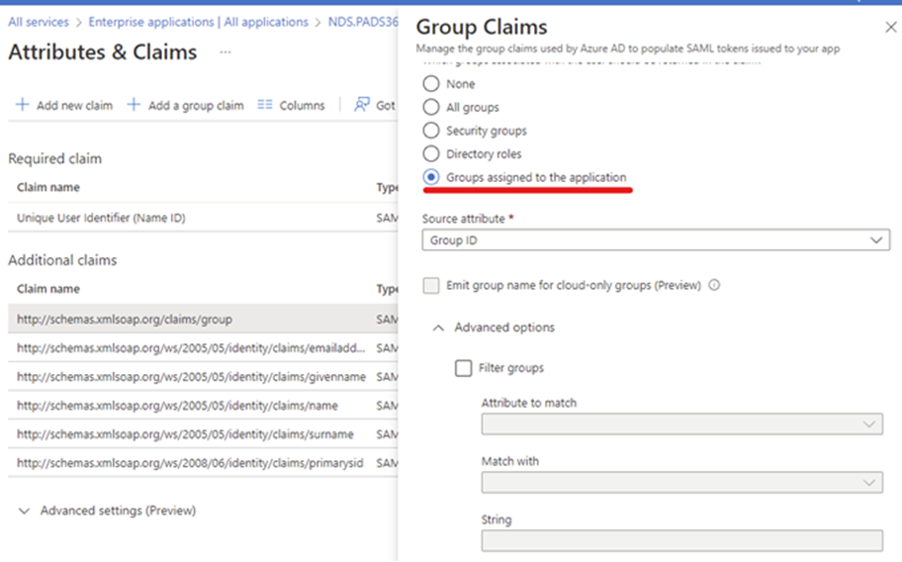
2. Attributes & Claims Setup
- While in Single sign-on, go to Attributes & Claims and click Edit.
- Ensure claims match the required structure for successful login.
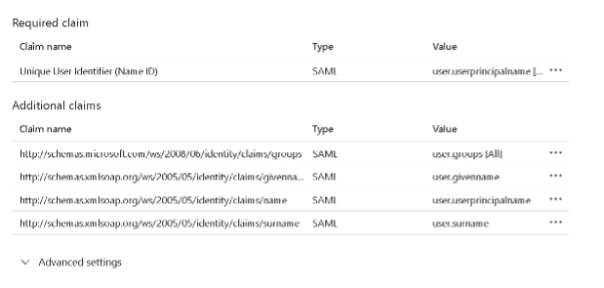
- Specifically, configure the group claim properly:
⚠️ If the group claim is misconfigured, the login will redirect with this error:
No account is defined for your authentication request
Access PADS4
- Log in to your PADS4 Dashboard in a web browser.
- Select Credentials from the left menu.
- Go to Providers > Identity > Microsoft Entra.
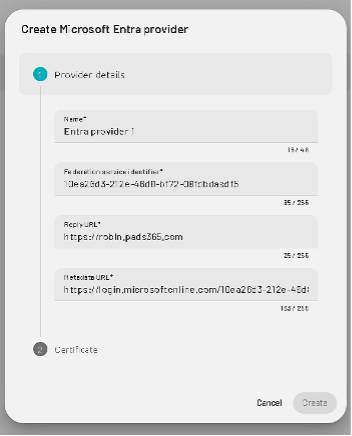
 Fill in the following fields using values from Azure:
Fill in the following fields using values from Azure:
-
Name: Friendly label shown on login page
-
Federation Service Identifier:
- From Single sign-on > Set up your_app section
- Copy the Azure AD Identifier
-
Reply URL:
Your PADS environment (e.g.,
https://pads4serverip)
-
Metadata URL:
- Found under SAML Certificates
- Copy the App Federation Metadata URL
-
Certificates:
- Upload the raw Microsoft Entra certificate (.cer)
- Upload the private key certificate (.pfx) used for HTTPS
Click Create to save.
4. Mappings & Group Management
- Go to Overview under Credentials.
- Click Connect, then New to create mappings and groups for this provider.
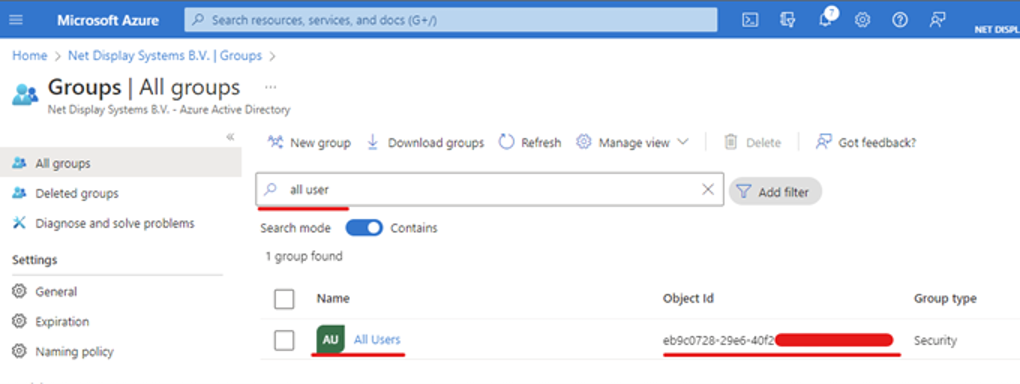
Find Group ID in Azure
- In portal.azure.com:
a. Go to Microsoft Entra ID
b. Select Groups
c. Search for your group
d. Copy the Object ID (this is the Group ID)
Create Group Mapping
- In PADS4, click New Group
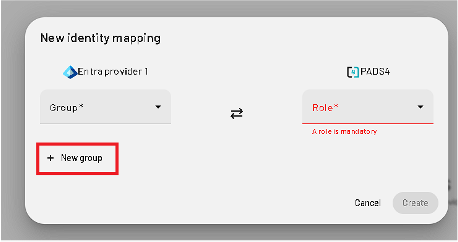
- Enter the copied Group ID
- Assign roles from the dropdown list
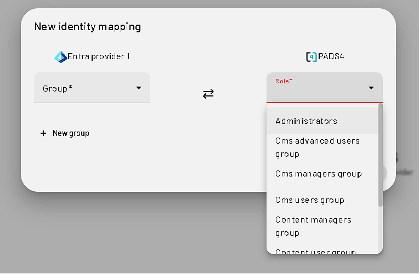
- Save the group. You can add multiple roles per group.
5. Finalizing SSO
- Logout and refresh the PADS4 Portal
- The SSO Login button should now be visible
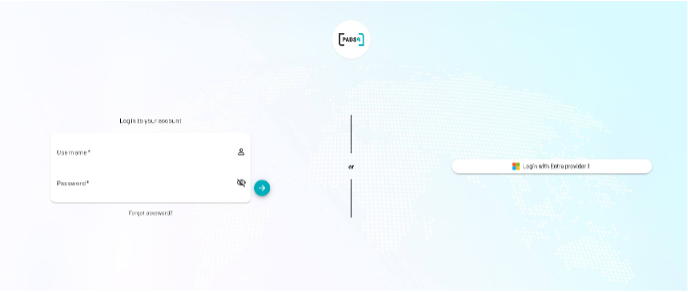
- You can now sign in using Azure credentials























