1. Configure mappings
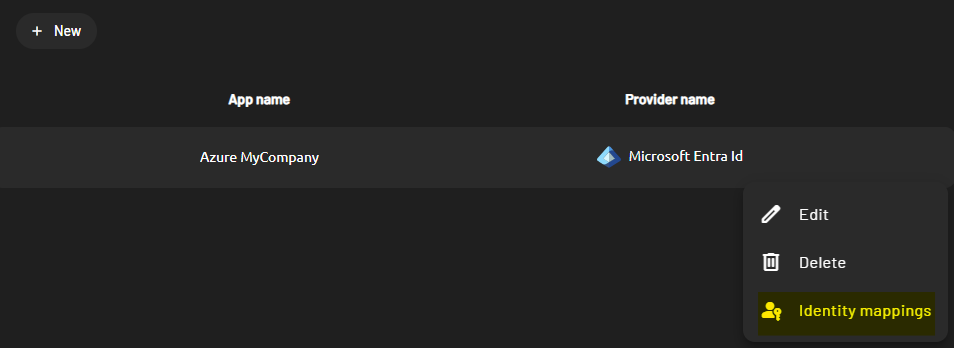
In order to configure these mappings:- On your newly created identity provider, click on “Identity mappings”
- On the current “Role mappings” tab, you will click on “New” to create a new role mapping relation

- On the role mapping form, you will have to fill two information
- The SSO provider group – which relates to the user group claim that you configured on the external identity provider
- The PADS4 roles – which determine the roles assigned to a user based on the external identity provider group they belong to
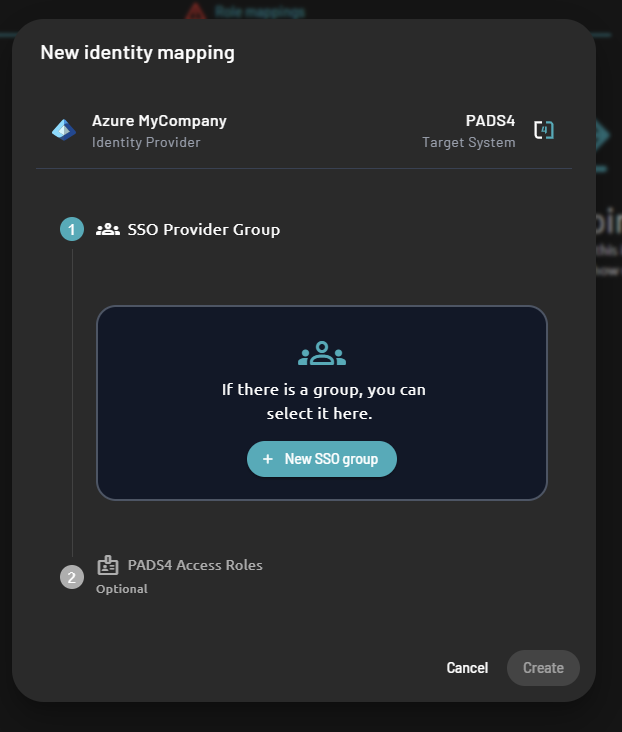
- Select a SSO Provider for your role mapping
- If the SSO Provider group you expect is not yet created, you can click on the “New SSO Group” button to add another group in the list
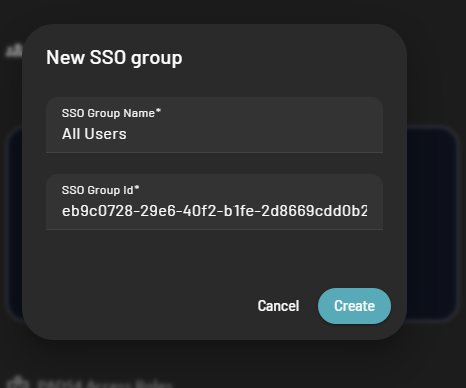
- The SSO Group Name is only used here to remember what is the identity of the group you created
- The SSO Group id should correspond to the group claim value that you did set up on the external identity provider claims configuration
- By default, the group claim value is :
- The user group id for Azure
- The user group name for Okta
- By default, the group claim value is :
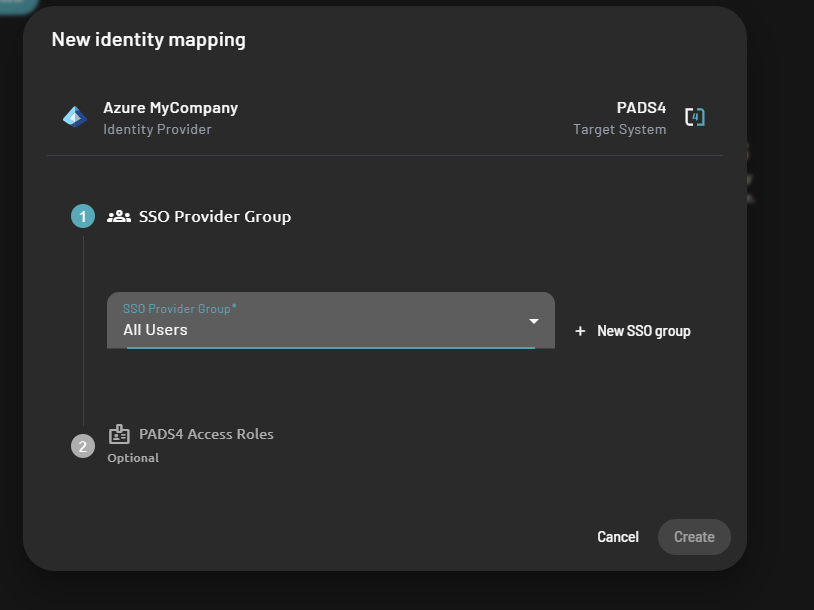
- Select roles on PADS4
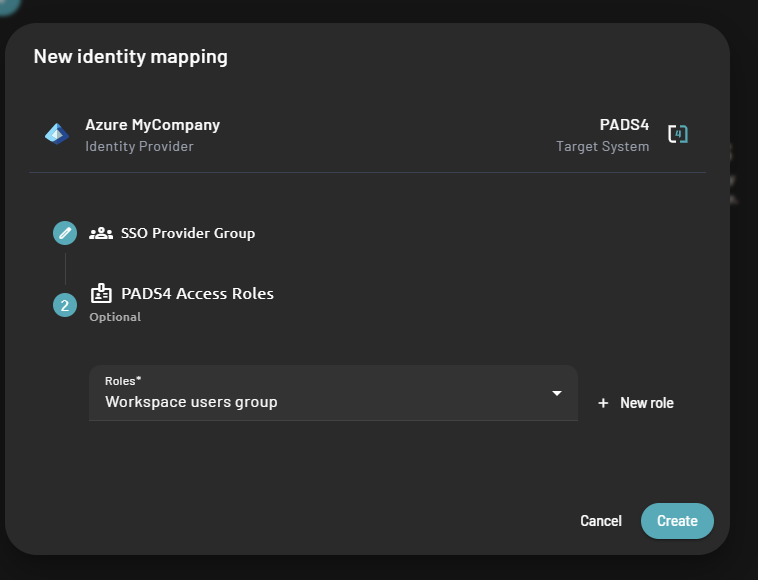
- Then click on the “Create” button save the role mapping.
- This process has to be repeated as much as you want to specify different external identity user group that you want to be allowed to the application.
2. Update identity provider claims (optional)
If you are creating your identity provider from a custom SAML 2.0 external identity provider or if you want to extend or update your claims attributes, you might want to edit the claims mapping on the pads4 identity provider you created. In order to update those claims, you will need to:- On your newly created identity provider, click on “Identity mappings”
- Then switch to the “Claims” tab.
If you created your identity provider from Azure or Okta, you might find here some default claims mapping that you can modify if required
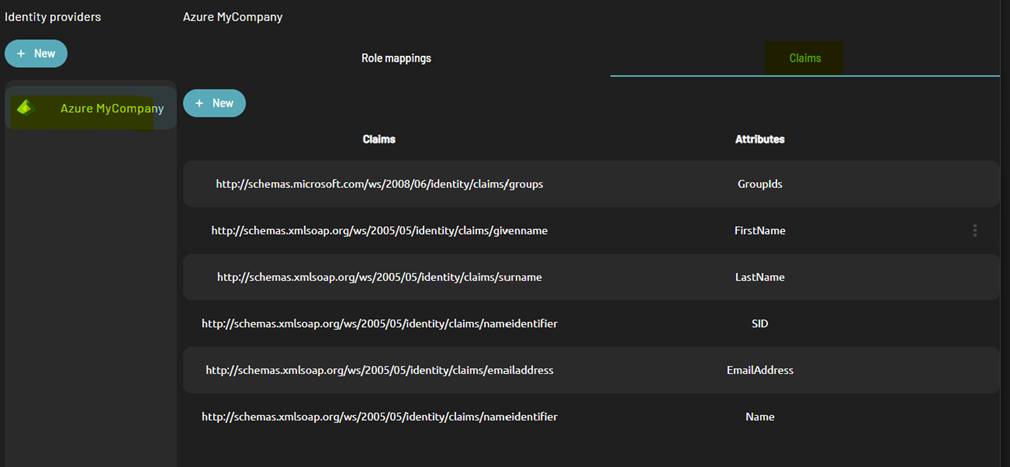
- Here you can either create a new claim or update an existing one, If you create a new claim, you will have to fill in the following information
- The claim name – which relates to the claim name that will be retrieved on the SAML response
- The local attribute – which determine the property that will be filled in with the claim value when the pads user will be created
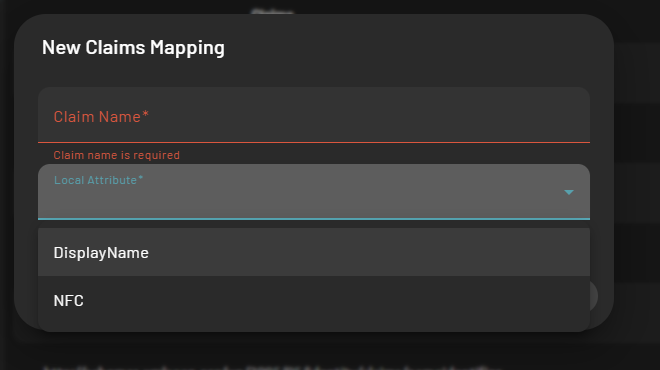
- The local attribute can only be chosen on a list of determined pads4 user properties listed below
| Local attribute | Description |
|---|---|
| GroupIds | Relates to the group ids retrieved for the role mapping association logic |
| FirstName | Relates to the first name property of the PADS4 user |
| SID | Relates the last name property of the PADS4 user |
| EmailAddress | Relates to a unique key that is the link between the user in the external identity provider and the user in PADS |
| Name | Relates the email property of the PADS4 user |
| DisplayName | Relates the login property of the PADS4 user |
| NFC | Relates the NFC property of the PADS4 user |

